Experimental designs. (A) INTERCEPT Blood System for RBCs. Leukoreduced... | Download Scientific Diagram
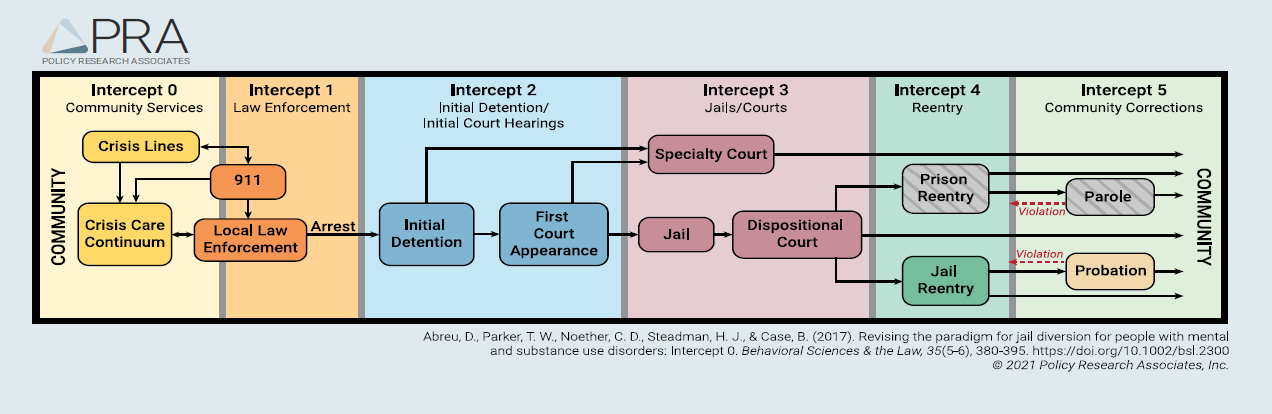
CHIPS Articles: How DoD is using the Risk Management Framework to assess operational risk for decertified cryptographic algorithms

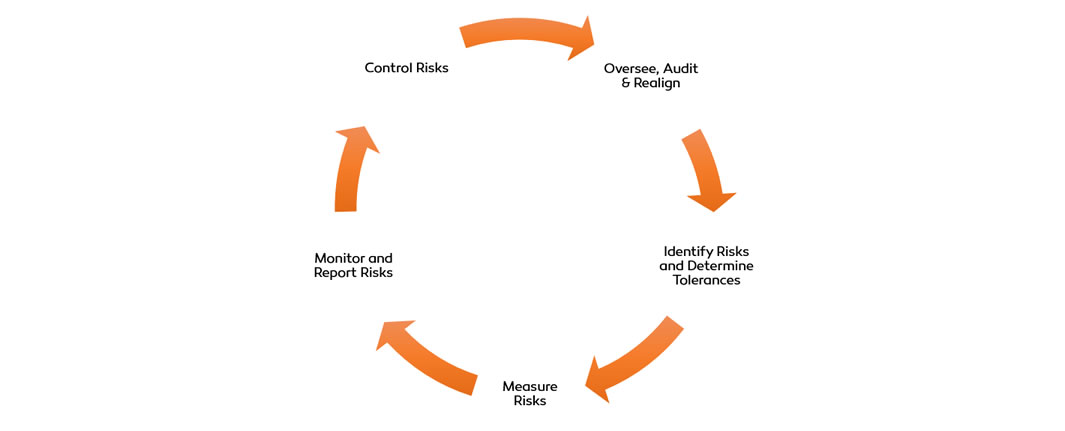
Business PPT Templates | Business PowerPoint Diagrams | Template PowerPoint Slides | PPT Presentations Backgrounds
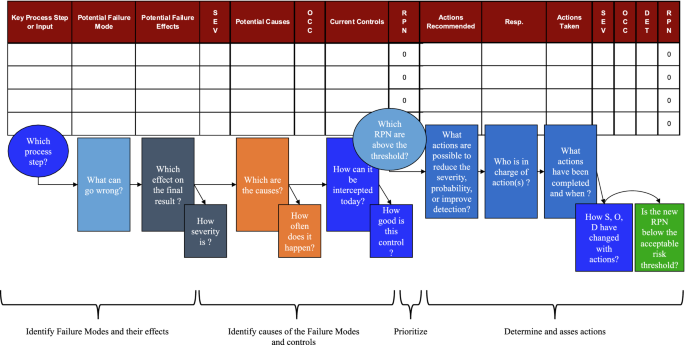
A failure mode and effect analysis (FMEA)-based approach for risk assessment of scientific processes in non-regulated research laboratories | Accreditation and Quality Assurance




:max_bytes(150000):strip_icc()/risk-control.asp-Final-d0dc2b8f24dd401c8cdc8cbd5ee12b33.jpg)



:max_bytes(150000):strip_icc()/risk-management-4189908-FINAL-2-976ae194e01848618ca94941ab9d2395.jpg)