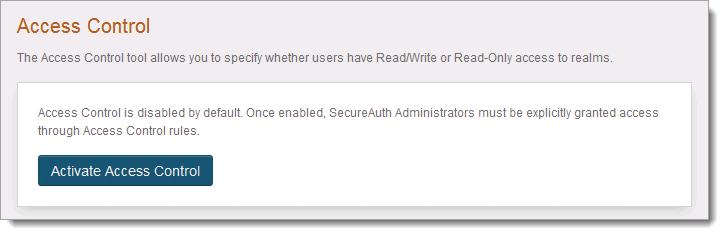
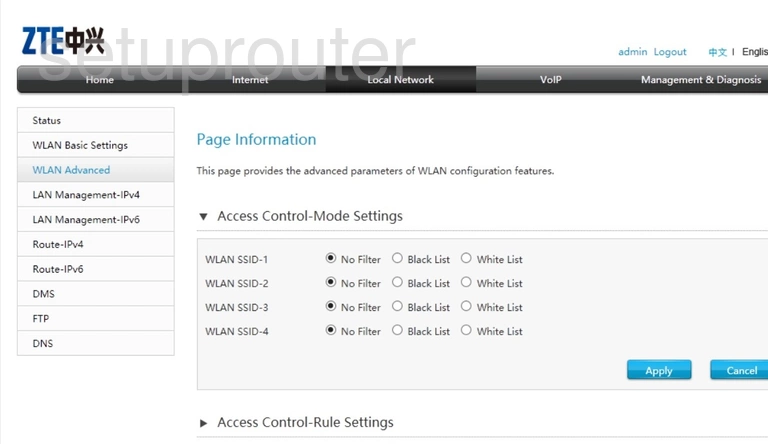
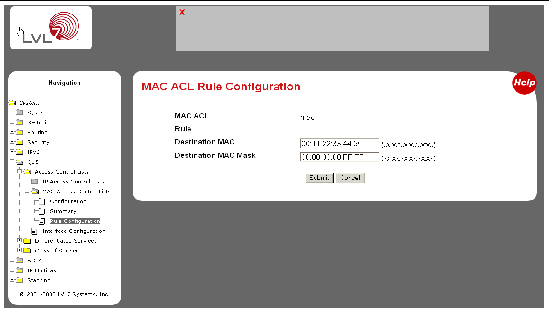
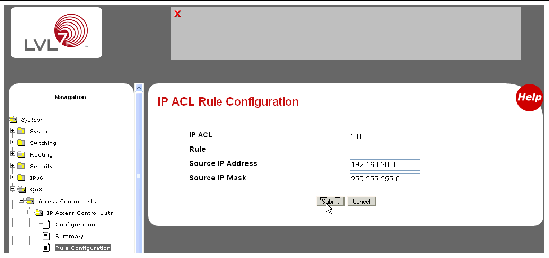
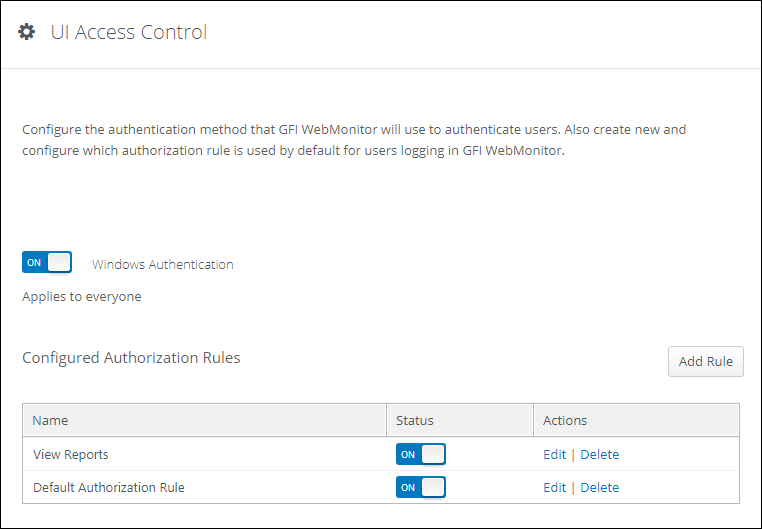
Configuring Geolocation Access Control Rules to Block or Allow Requests from Specific Locations_Web Application Firewall_User Guide_Policies

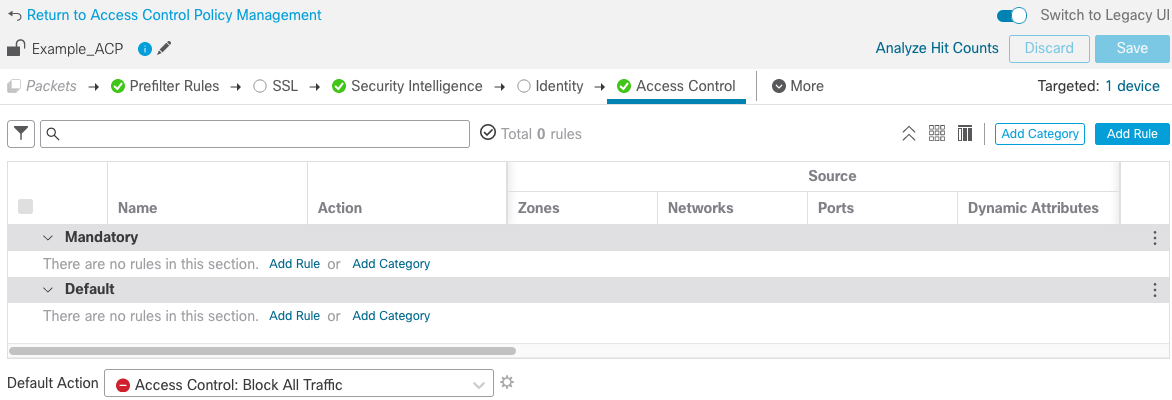
Which subset of access control rules on DB can ensure confidentiality... | Download Scientific Diagram





.jpg)

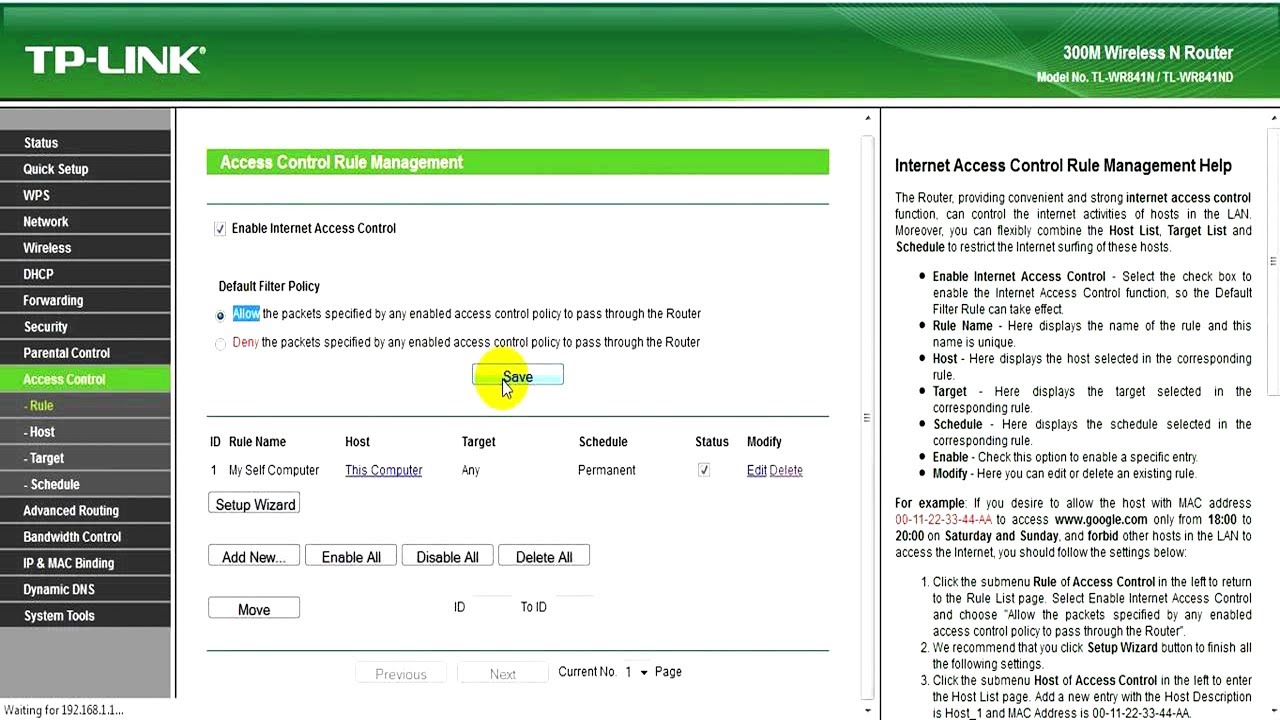
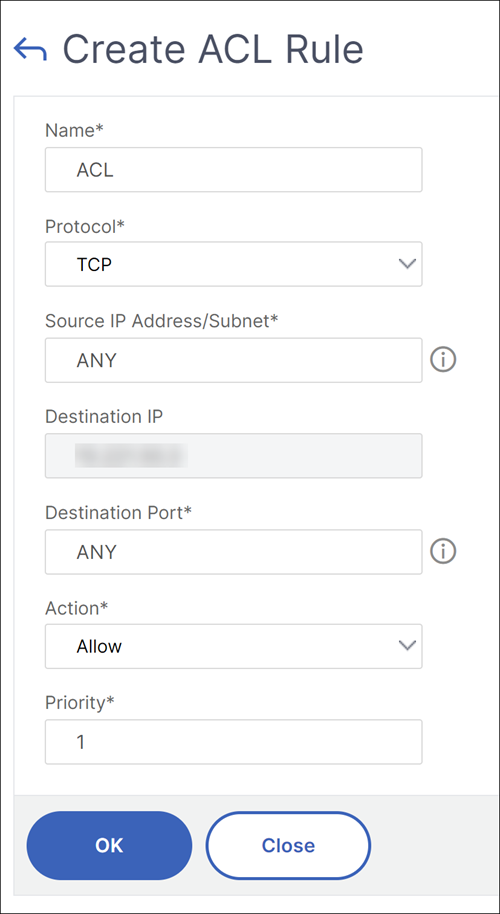

![Defining access control [PRO] Defining access control [PRO]](https://gatographql.com/assets/guides/upstream-pro/access-control-list.png)